About Data Kawach
What is Data Kawach?
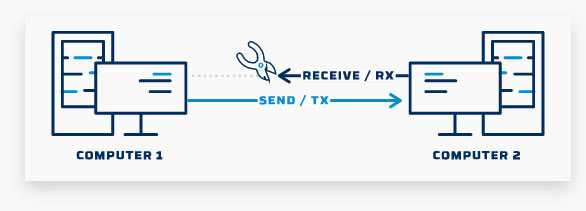
A data kawach is a cybersecurity solution that ensures unidirectional information exchange. This high assurance hardware device maintains both network integrity by preventing intrusion, as well as network confidentiality by protecting the most security-sensitive information.By using a data kawach, you can ensure that the transfer is done securely without jeopardizing the integrity or the confidentiality of the network.
Data Kawach is an electronic device that allows current to flow in one direction only. Similarly, Data Kawach technology lets information flow safely in only one direction, from secure areas to less secure systems, without permitting reverse access.Every organization that operates with sensitive information has great use of a data kawach to protect its valuable information and securely exchange data. By transferring information via a data kawach, you are guaranteed that no one can use the same connection in the opposite direction to reach the high-security network and disrupt the availability and integrity of the systems.
How does Data Kawach technology work?
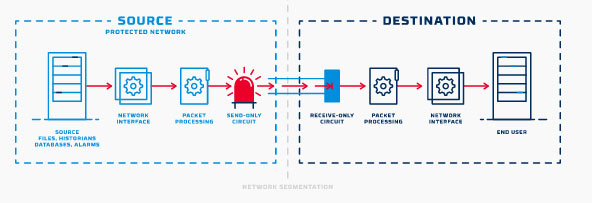
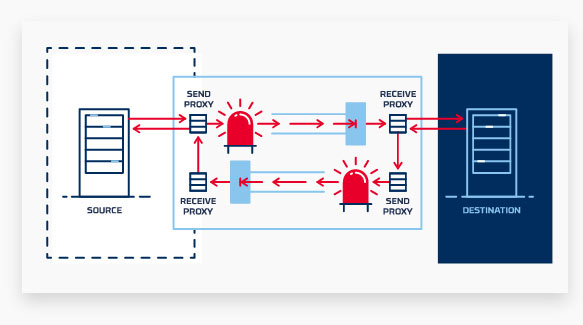
A data kawach is a security product that is located among networks and acts as a non-return valve whose function best permits records to be sent in a single route at the same time as blocking all statistics inside the contrary path. Data kawach is a hybrid device, also called a “unidirectional security gateway”, which sits between two networks. Working like a check valve, the function of a Data Kawach is to allow all data to pass in the forward direction while blocking all data in the reverse direction.
Because it is only physically capable of sending data one-way, a Data Kawach creates a physical barrier or “air gap” between the two points. This prevents data leakage, eliminates the threat of malware, and fully protects the sending network from external threats through Data Kawach’s network path. The other consequence of this one-way path is that the protocol is “broken” between the sending and receiving domains to accommodate a one-way protocol connection.
If a Data Kawach is directed out from the high-security network towards a network with a lower security level, data can be transferred while the network stays protected. By transferring information via a Data Kawach, you are guaranteed that no one can use the same connection in the opposite direction to reach the secure network and manipulate its environment.
What are Data Kawach used for?
Data kawach is used to segment and defend networks and transfer information in one direction. They allow data to be sent from a secured network/segment to external systems and users (e.g. the cloud, a remote monitoring facility, regulatory bodies), without creating a threat vector back into the secured network. Data kawach can be used to protect network segments of all sizes, from a single controller to an entire facility.
Critical infrastructure operators, industrial companies, military commands, intelligence organizations, and even commercial companies such as financial institutions use Data Kawach to provide reliable, hardware-enforced security for their systems and networks.
Why Choose Data Kawach?
Data Kawach covers many different areas, including access control, cloud security, malware protection, BYOD security, remote workforce, and web security. The modern digital business of any size, industry, or location needs to keep up with all these responsibilities to maintain a strong security posture. Data Kawach is a forward-thinking nonprofit with a mission “to make the connected world a safer place by developing, validating, and promoting timely best practice solutions that help people, businesses, and governments protect themselves against pervasive cyber threats.”
Data Kawach
Data Kawach is a dedicated cyber security expert. We are guided by our mission to derive satisfaction from helping to create a more secure society with the help of our technical and innovative solutions.
Data Kawach covers many different areas, including access control, cloud security, malware protection, BYOD security, remote workforce, and web security.
+ Risk Management.
+ We work with and create confidential information .
+ To lead the way in innovation.
+ Handle risk the right way
+ Provides your team with the guidance, processes, and technology.